11 - Identity in Rest API
Rest identity
No cookies in AJAX requests
No Rest controllers in ASP.NET Core for Identity
Industrial strength solutions
- https://www.keycloak.org
- authentik
- Authelia
- Zitadel
JWT
No Cookies! (Sometimes confusing when you do both normal web and Rest API-s from the same server)
Ajax uses JSON Web Tokens (JWT) – RFC 7519
- Test and verify on https://jwt.io
- Digitally signed (usually not encrypted) - HMAC, RSA, ECDSA
- HTTPS is mandatory
JWT Format
- Format: Header.Payload.Signature
- Every part is Base64Url encoded
- Header: Type and Signing algorithm
- Payload: Claims (registered, public, private)
- Signature: createSignature(Header + "." + Payload, secret)
JWT based auth
-
In authentication, when the user successfully logs in using their credentials, a JSON Web Token will be returned. Since tokens are credentials, great care must be taken to prevent security issues.
-
Whenever the user wants to access a protected route or resource, the user agent should send the JWT, typically in the Authorization header using the Bearer schema.
Authorization: Bearer <token>
- If the token is sent in the Authorization header, Cross-Origin Resource Sharing (CORS) won't be an issue as it doesn't use cookies.
Token auth simple flow
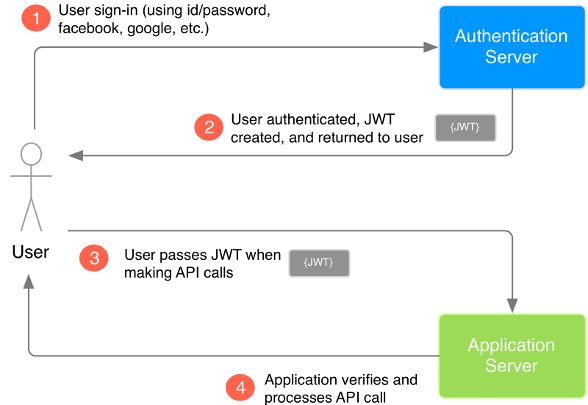
JWT problems
With signed tokens, all the information contained within the token is exposed to users or other parties, even though they are unable to change it.
JWT simple implementation
Configure app settings for JWT (add new section)
"JWT": {
"Key": "some_secret_password_dont_share.123",
"Issuer": "itcollege.taltech.ee",
"ExpireDays": 30
}
Add JWT auth and Cookie auth support
Install via unget Microsoft.AspNetCore.Authentication.JwtBearer;
JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Clear(); // => remove default claims
Services
.AddAuthentication()
.AddCookie(options => { options.SlidingExpiration = true; })
.AddJwtBearer(cfg =>
{
cfg.RequireHttpsMetadata = false;
cfg.SaveToken = true;
cfg.TokenValidationParameters = new TokenValidationParameters
{
ValidIssuer = Configuration["JWT:Issuer"],
ValidAudience = Configuration["JWT:Issuer"],
IssuerSigningKey = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(Configuration["JWT:Key"])),
ClockSkew = TimeSpan.Zero // remove delay of token when expire
};
});
If no cookie support is needed, make JWT auth default
// =============== JWT support ===============
JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Clear(); // => remove default claims
Services
.AddAuthentication(options =>
{
options.DefaultAuthenticateScheme = JwtBearerDefaults.AuthenticationScheme;
options.DefaultScheme = JwtBearerDefaults.AuthenticationScheme;
options.DefaultChallengeScheme = JwtBearerDefaults.AuthenticationScheme;
})
.AddCookie(options => { options.SlidingExpiration = true; })
.AddJwtBearer(cfg =>
{
cfg.RequireHttpsMetadata = false;
cfg.SaveToken = true;
cfg.TokenValidationParameters = new TokenValidationParameters
{
ValidIssuer = Configuration["JwtIssuer"],
ValidAudience = Configuration["JwtIssuer"],
IssuerSigningKey = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(Configuration["JwtKey"])),
ClockSkew = TimeSpan.Zero // remove delay of token when expire
};
});
Generate JWT
-
Add controller for register and login Rest calls - return token on success
-
Create method to generate JWT tokens
public static string GenerateJwt(IEnumerable<Claim> claims, string key, string issuer, int expiresInDays)
{
var signingKey = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(key));
var signingCredentials = new SigningCredentials(signingKey, SecurityAlgorithms.HmacSha256);
var expires = DateTime.Now.AddDays(expiresInDays);
var token = new JwtSecurityToken(
issuer: issuer,
audience: issuer,
claims: claims,
expires: expires,
signingCredentials: signingCredentials
);
return new JwtSecurityTokenHandler().WriteToken(token);
}
Use token
On web api request, include token in header
Authorization: Bearer eyJhbGciOiJIUzI1NiIsI.....- In web-api controllers – use the same methods and attributes, as in the pure html/MVC side.
[Authorize]will use the authorization mechanism in the same order, as the are added to middleware (so cookie auth can be first - bad for REST)- Force use of specific schema
[Authorize(AuthenticationSchemes = JwtBearerDefaults.AuthenticationScheme)]
Token auth with refresh
Token will finally expire - in more secure apps token lifetime is really short (1 minute).
To avoid constant login, another token is used - refresh token (random guid for example).
Refresh token lifetime is much longer (days).
When token expiration is detected, user can request new token by sending old token and refresh token to refesh endpoint.
User info is extracted from old token, then from permanent storage (IdenityUser) user info is retrieved along with refresh token info (value end expiration time).
When user supplied refresh token matches with stored refresh token - new token and refresh token (refresh token rotation) is issued.
Some grace period might be need (up to 60 seconds) before revoking old refresh token.
If user logs-in from multiple instances - refresh token collection.
public class AppUser : IdentityUser<Guid>
{
public string? RefreshToken { get; set; }
public DateTime RefreshTokenExpiryTime { get; set; }
}
ASPNET Core Identity methods
var appUser = await _userManager.FindByEmailAsync(dto.Email);
var result = await _signInManager.CheckPasswordSignInAsync(appUser, dto.Password, false);
var result = await _userManager.CreateAsync(appUser, dto.Password);
var claimsPrincipal = await _signInManager.CreateUserPrincipalAsync(appUser);
Full code for api identity controller
Implementation for token auth with refresh
using System.Configuration;
using System.IdentityModel.Tokens.Jwt;
using System.Net;
using System.Security.Claims;
using App.DAL.EF;
using App.Domain.Identity;
using App.DTO.v1_0;
using App.DTO.v1_0.Identity;
using Asp.Versioning;
using Helpers;
using Microsoft.AspNetCore.Authentication.JwtBearer;
using Microsoft.AspNetCore.Authorization;
using Microsoft.AspNetCore.Identity;
using Microsoft.AspNetCore.Mvc;
using Microsoft.EntityFrameworkCore;
namespace WebApp.ApiControllers.Identity;
[ApiVersion("1.0")]
[ApiVersion("0.9", Deprecated = true)]
[ApiController]
[Route("/api/v{version:apiVersion}/identity/[controller]/[action]")]
public class AccountController : ControllerBase
{
private readonly UserManager<AppUser> _userManager;
private readonly ILogger<AccountController> _logger;
private readonly SignInManager<AppUser> _signInManager;
private readonly IConfiguration _configuration;
private readonly AppDbContext _context;
public AccountController(UserManager<AppUser> userManager, ILogger<AccountController> logger,
SignInManager<AppUser> signInManager, IConfiguration configuration, AppDbContext context)
{
_userManager = userManager;
_logger = logger;
_signInManager = signInManager;
_configuration = configuration;
_context = context;
}
/// <summary>
/// Register new local user into app.
/// </summary>
/// <param name="registrationData">Username and password. And personal details.</param>
/// <param name="expiresInSeconds">Override jwt lifetime for testing.</param>
/// <returns>JWTResponse - jwt and refresh token</returns>
[HttpPost]
[Produces("application/json")]
[Consumes("application/json")]
[ProducesResponseType<JWTResponse>((int) HttpStatusCode.OK)]
[ProducesResponseType<RestApiErrorResponse>((int) HttpStatusCode.BadRequest)]
public async Task<ActionResult<JWTResponse>> Register(
[FromBody]
RegisterInfo registrationData,
[FromQuery]
int expiresInSeconds)
{
if (expiresInSeconds <= 0) expiresInSeconds = int.MaxValue;
expiresInSeconds = expiresInSeconds < _configuration.GetValue<int>("JWT:expiresInSeconds")
? expiresInSeconds
: _configuration.GetValue<int>("JWT:expiresInSeconds");
// is user already registered
var appUser = await _userManager.FindByEmailAsync(registrationData.Email);
if (appUser != null)
{
_logger.LogWarning("User with email {} is already registered", registrationData.Email);
return BadRequest(
new RestApiErrorResponse()
{
Status = HttpStatusCode.BadRequest,
Error = $"User with email {registrationData.Email} is already registered"
}
);
}
// register user
var refreshToken = new AppRefreshToken();
appUser = new AppUser()
{
Email = registrationData.Email,
UserName = registrationData.Email,
FirstName = registrationData.Firstname,
LastName = registrationData.Lastname,
RefreshTokens = new List<AppRefreshToken>() {refreshToken}
};
refreshToken.AppUser = appUser;
var result = await _userManager.CreateAsync(appUser, registrationData.Password);
if (!result.Succeeded)
{
return BadRequest(
new RestApiErrorResponse()
{
Status = HttpStatusCode.BadRequest,
Error = result.Errors.First().Description
}
);
}
// save into claims also the user full name
result = await _userManager.AddClaimsAsync(appUser, new List<Claim>()
{
new(ClaimTypes.GivenName, appUser.FirstName),
new(ClaimTypes.Surname, appUser.LastName)
});
if (!result.Succeeded)
{
return BadRequest(
new RestApiErrorResponse()
{
Status = HttpStatusCode.BadRequest,
Error = result.Errors.First().Description
}
);
}
// get full user from system with fixed data (maybe there is something generated by identity that we might need
appUser = await _userManager.FindByEmailAsync(appUser.Email);
if (appUser == null)
{
_logger.LogWarning("User with email {} is not found after registration", registrationData.Email);
return BadRequest(
new RestApiErrorResponse()
{
Status = HttpStatusCode.BadRequest,
Error = $"User with email {registrationData.Email} is not found after registration"
}
);
}
var claimsPrincipal = await _signInManager.CreateUserPrincipalAsync(appUser);
var jwt = IdentityHelpers.GenerateJwt(
claimsPrincipal.Claims,
_configuration.GetValue<string>("JWT:key"),
_configuration.GetValue<string>("JWT:issuer"),
_configuration.GetValue<string>("JWT:audience"),
expiresInSeconds
);
var res = new JWTResponse()
{
Jwt = jwt,
RefreshToken = refreshToken.RefreshToken,
};
return Ok(res);
}
[HttpPost]
public async Task<ActionResult<JWTResponse>> Login(
[FromBody]
LoginInfo loginInfo,
[FromQuery]
int expiresInSeconds
)
{
if (expiresInSeconds <= 0) expiresInSeconds = int.MaxValue;
expiresInSeconds = expiresInSeconds < _configuration.GetValue<int>("JWT:expiresInSeconds")
? expiresInSeconds
: _configuration.GetValue<int>("JWT:expiresInSeconds");
// verify user
var appUser = await _userManager.FindByEmailAsync(loginInfo.Email);
if (appUser == null)
{
_logger.LogWarning("WebApi login failed, email {} not found", loginInfo.Email);
// TODO: random delay
return NotFound("User/Password problem");
}
// verify password
var result = await _signInManager.CheckPasswordSignInAsync(appUser, loginInfo.Password, false);
if (!result.Succeeded)
{
_logger.LogWarning("WebApi login failed, password {} for email {} was wrong", loginInfo.Password,
loginInfo.Email);
// TODO: random delay
return NotFound("User/Password problem");
}
var claimsPrincipal = await _signInManager.CreateUserPrincipalAsync(appUser);
if (claimsPrincipal == null)
{
_logger.LogWarning("WebApi login failed, claimsPrincipal null");
// TODO: random delay
return NotFound("User/Password problem");
}
if (!_context.Database.ProviderName!.Contains("InMemory"))
{
var deletedRows = await _context.RefreshTokens
.Where(t => t.AppUserId == appUser.Id && t.ExpirationDT < DateTime.UtcNow)
.ExecuteDeleteAsync();
_logger.LogInformation("Deleted {} refresh tokens", deletedRows);
}
else
{
//TODO: inMemory delete for testing
}
var refreshToken = new AppRefreshToken()
{
AppUserId = appUser.Id
};
_context.RefreshTokens.Add(refreshToken);
await _context.SaveChangesAsync();
var jwt = IdentityHelpers.GenerateJwt(
claimsPrincipal.Claims,
_configuration.GetValue<string>("JWT:key"),
_configuration.GetValue<string>("JWT:issuer"),
_configuration.GetValue<string>("JWT:audience"),
expiresInSeconds
);
var responseData = new JWTResponse()
{
Jwt = jwt,
RefreshToken = refreshToken.RefreshToken
};
return Ok(responseData);
}
[HttpPost]
public async Task<ActionResult<JWTResponse>> RefreshTokenData(
[FromBody]
TokenRefreshInfo tokenRefreshInfo,
[FromQuery]
int expiresInSeconds
)
{
if (expiresInSeconds <= 0) expiresInSeconds = int.MaxValue;
expiresInSeconds = expiresInSeconds < _configuration.GetValue<int>("JWT:expiresInSeconds")
? expiresInSeconds
: _configuration.GetValue<int>("JWT:expiresInSeconds");
// extract jwt object
JwtSecurityToken? jwt;
try
{
jwt = new JwtSecurityTokenHandler().ReadJwtToken(tokenRefreshInfo.Jwt);
if (jwt == null)
{
return BadRequest(
new RestApiErrorResponse()
{
Status = HttpStatusCode.BadRequest,
Error = "No token"
}
);
}
}
catch (Exception e)
{
return BadRequest(new RestApiErrorResponse()
{
Status = HttpStatusCode.BadRequest,
Error = "No token"
}
);
}
// validate jwt, ignore expiration date
if (!IdentityHelpers.ValidateJWT(
tokenRefreshInfo.Jwt,
_configuration.GetValue<string>("JWT:key"),
_configuration.GetValue<string>("JWT:issuer"),
_configuration.GetValue<string>("JWT:audience")
))
{
return BadRequest("JWT validation fail");
}
var userEmail = jwt.Claims.FirstOrDefault(x => x.Type == ClaimTypes.Email)?.Value;
if (userEmail == null)
{
return BadRequest(
new RestApiErrorResponse()
{
Status = HttpStatusCode.BadRequest,
Error = "No email in jwt"
}
);
}
var appUser = await _userManager.FindByEmailAsync(userEmail);
if (appUser == null)
{
return NotFound("User with email {userEmail} not found");
}
// load and compare refresh tokens
await _context.Entry(appUser).Collection(u => u.RefreshTokens!)
.Query()
.Where(x =>
(x.RefreshToken == tokenRefreshInfo.RefreshToken && x.ExpirationDT > DateTime.UtcNow) ||
(x.PreviousRefreshToken == tokenRefreshInfo.RefreshToken &&
x.PreviousExpirationDT > DateTime.UtcNow)
)
.ToListAsync();
if (appUser.RefreshTokens == null || appUser.RefreshTokens.Count == 0)
{
return NotFound(
new RestApiErrorResponse()
{
Status = HttpStatusCode.NotFound,
Error = $"RefreshTokens collection is null or empty - {appUser.RefreshTokens?.Count}"
}
);
}
if (appUser.RefreshTokens.Count != 1)
{
return NotFound("More than one valid refresh token found");
}
// get claims based user
var claimsPrincipal = await _signInManager.CreateUserPrincipalAsync(appUser);
if (claimsPrincipal == null)
{
_logger.LogWarning("Could not get ClaimsPrincipal for user {}", userEmail);
return NotFound(
new RestApiErrorResponse()
{
Status = HttpStatusCode.BadRequest,
Error = "User/Password problem"
}
);
}
// generate jwt
var jwtResponseStr = IdentityHelpers.GenerateJwt(
claimsPrincipal.Claims,
_configuration.GetValue<string>("JWT:key"),
_configuration.GetValue<string>("JWT:issuer"),
_configuration.GetValue<string>("JWT:audience"),
expiresInSeconds
);
// make new refresh token, keep old one still valid for some time
var refreshToken = appUser.RefreshTokens.First();
if (refreshToken.RefreshToken == tokenRefreshInfo.RefreshToken)
{
refreshToken.PreviousRefreshToken = refreshToken.RefreshToken;
refreshToken.PreviousExpirationDT = DateTime.UtcNow.AddMinutes(1);
refreshToken.RefreshToken = Guid.NewGuid().ToString();
refreshToken.ExpirationDT = DateTime.UtcNow.AddDays(7);
await _context.SaveChangesAsync();
}
var res = new JWTResponse()
{
Jwt = jwtResponseStr,
RefreshToken = refreshToken.RefreshToken,
};
return Ok(res);
}
[Authorize(AuthenticationSchemes = JwtBearerDefaults.AuthenticationScheme)]
[HttpPost]
public async Task<ActionResult> Logout(
[FromBody]
LogoutInfo logout)
{
// delete the refresh token - so user is kicked out after jwt expiration
// We do not invalidate the jwt on serverside - that would require pipeline modification and checking against db on every request
// so client can actually continue to use the jwt until it expires (keep the jwt expiration time short ~1 min)
var userIdStr = _userManager.GetUserId(User);
if (userIdStr == null)
{
return BadRequest(
new RestApiErrorResponse()
{
Status = HttpStatusCode.BadRequest,
Error = "Invalid refresh token"
}
);
}
if (Guid.TryParse(userIdStr, out var userId))
{
return BadRequest("Deserialization error");
}
var appUser = await _context.Users
.Where(u => u.Id == userId)
.SingleOrDefaultAsync();
if (appUser == null)
{
return NotFound(
new RestApiErrorResponse()
{
Status = HttpStatusCode.NotFound,
Error = "User/Password problem"
}
);
}
await _context.Entry(appUser)
.Collection(u => u.RefreshTokens!)
.Query()
.Where(x =>
(x.RefreshToken == logout.RefreshToken) ||
(x.PreviousRefreshToken == logout.RefreshToken)
)
.ToListAsync();
foreach (var appRefreshToken in appUser.RefreshTokens!)
{
_context.RefreshTokens.Remove(appRefreshToken);
}
var deleteCount = await _context.SaveChangesAsync();
return Ok(new {TokenDeleteCount = deleteCount});
}
}
Domain entity fo refresh tokens
using System.ComponentModel.DataAnnotations;
namespace Base.Domain;
public class BaseRefreshToken : BaseRefreshToken<Guid>
{
}
public class BaseRefreshToken<TKey> : BaseEntityId<TKey>
where TKey : IEquatable<TKey>
{
[MaxLength(64)]
public string RefreshToken { get; set; } = Guid.NewGuid().ToString();
public DateTime ExpirationDT { get; set; } = DateTime.UtcNow.AddDays(7);
[MaxLength(64)]
public string? PreviousRefreshToken { get; set; }
public DateTime PreviousExpirationDT { get; set; } = DateTime.UtcNow.AddDays(7);
}
using Base.Domain;
namespace App.Domain.Identity;
public class AppRefreshToken : BaseRefreshToken
{
public Guid AppUserId { get; set; }
public AppUser? AppUser { get; set; }
}
DbSet for refresh tokens
public DbSet<AppRefreshToken> RefreshTokens { get; set; } = default!;
Reference in appuse.
public ICollection<AppRefreshToken>? RefreshTokens { get; set; }